OverTheWire Wargames bandit => 2
OverTheWire is a platform that provides a collection of wargames designed to help individuals enhance their knowledge of cybersecurity. It’s ideal for both beginners and experienced security enthusiasts looking to expand their skill set in a practical and engaging way.
The platform’s wargames are structured to help users progress step-by-step, starting with basic tasks and advancing to more complex challenges. This makes it an excellent tool for learning concepts such as:
- Linux/Unix Basics: It introduces beginners to command-line tasks, file manipulation, and system navigation, providing a solid foundation in operating systems.
- Networking and Protocols: Challenges related to TCP/IP, HTTP, and other networking protocols teach how to analyze and interact with network traffic, offering insight into penetration testing techniques.
- Cryptography: OverTheWire covers fundamental cryptographic concepts, teaching users how to exploit weaknesses in encryption systems and improve their understanding of security protocols.
- Web Security: The platform includes practical lessons on common web vulnerabilities such as SQL Injection, Cross-Site Scripting (XSS), and other issues that are crucial for web application security.
- Reverse Engineering: Users can dive into reverse engineering challenges to understand how to disassemble and manipulate programs, gaining valuable insight into software vulnerabilities.
- Forensics: OverTheWire also helps users build skills in digital forensics by analyzing compromised data, investigating file systems, and extracting hidden information.
Bandit, the most popular wargame on OverTheWire, is a great starting point for beginners. It introduces users to basic security concepts and Linux commands, offering a fun, interactive way to start learning. As players progress through the game, they tackle increasingly challenging puzzles that simulate real-world hacking scenarios.
In essence, OverTheWire offers a unique, hands-on learning experience where users can practice ethical hacking in a safe, controlled environment. Whether you’re looking to break into the world of cybersecurity or deepen your existing knowledge, OverTheWire provides a wealth of challenges to help you sharpen your skills.
This is a continuation from Part 2 of the Bandit Wargame series. If you haven’t checked out Part 1 blog, I highly recommend giving it a read before proceeding, as it covers foundational skills essential for tackling these levels.
Now, let’s pick up where we left off and dive deeper into the challenges, starting from Bandit Level 11. These levels will introduce more advanced concepts, helping you sharpen your Linux skills further. Let’s get started!
Bandit Level 11 → Level 12
Level Goal
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
1
2
3
4
5
bandit11@bandit:~$ cat data.txt
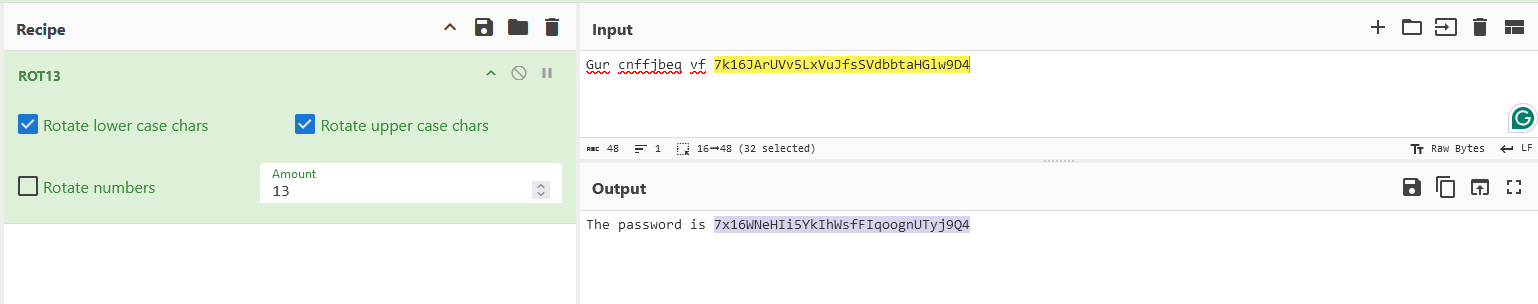
Gur cnffjbeq vf 7k16JArUVv5LxVuJfsSVdbbtaHGlw9D4
bandit11@bandit:~$ cat data.txt | tr 'A-Za-z' 'N-ZA-Mn-za-m'
The password is 7x16WNeHIi5YkIhWsfFIqoognUTyj9Q4
bandit11@bandit:~$
Explanaiton
the tr (translate) command in Linux or Unix-like systems to perform a character-by-character transformation of text. Specifically, this command implements the ROT13 cipher for encoding or decoding text.
ROT13 (short for “rotate by 13 places”) is a simple letter substitution cipher used primarily for obscuring text. It replaces each letter of the alphabet with the letter 13 positions ahead of it. Since there are 26 letters in the English alphabet, applying ROT13 twice (rotating 13 positions forward and then 13 positions back) restores the original text.
For example:
- “A” becomes “N”
- “B” becomes “O”
- “C” becomes “P”
- “Z” becomes “M”
The beauty of ROT13 is its simplicity. It is often used in online forums or email to obscure spoilers, puzzle answers, or sensitive information, as it does not provide real encryption but just hides the content in plain view.
Bandit Level 12 → Level 13
Level Goal
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work. Use mkdir with a hard to guess directory name. Or better, use the command “mktemp -d”. Then copy the datafile using cp, and rename it using mv (read the manpages!)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
bandit12@bandit:~$ mktemp -d
/tmp/tmp.1gzcyg61Ek
bandit12@bandit:~$ cd /tmp/tmp.1gzcyg61Ek
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ cp ~/data.txt .
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ xxd -r data.txt binary
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file binary
binary: gzip compressed data, was "data2.bin", last modified: Thu Sep 19 07:08:15 2024, max compression, from Unix, original size modulo 2^32 574
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ mv binary binary.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ gzip -d binary.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file binary
binary: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ mv binary binary.bz2
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ bzip2 -d binary.bz2
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file binary
binary: gzip compressed data, was "data4.bin", last modified: Thu Sep 19 07:08:15 2024, max compression, from Unix, original size modulo 2^32 20480
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ mv binary binary.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ gzip -d binary.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file binary
binary: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ tar -xf binary
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data5.bin data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ tar -xf data5.bin
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data5.bin data6.bin data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ mv data6.bin data6.bz2
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ bzip2 -d data6.bz2
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data5.bin data6 data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file data6
data6: POSIX tar archive (GNU)
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ tar -xf data6
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data5.bin data6 data8.bin data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Thu Sep 19 07:08:15 2024, max compression, from Unix, original size modulo 2^32 49
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ mv data8.bin data8.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ gzip -d data8.gz
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ ls
binary data5.bin data6 data8 data.txt
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ file data8
data8: ASCII text
bandit12@bandit:/tmp/tmp.1gzcyg61Ek$ cat data8
The password is FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn
Explanation
- Create a temp directory using
mktemp -d, copydata.txtinto it and reverse the hex dump withxxd -rto get thebinaryfile. - Identify the file type with
fileand decompress or extract it repeatedly based on its format:- For gzip: Rename with
.gzand decompress usinggzip -d. - For bzip2: Rename with
.bz2and decompress usingbzip2 -d. - For tar archives: Extract using
tar -xf.
- For gzip: Rename with
- Repeat the process (analyzing and decompressing/extracting) until reaching the final file.
- Read the final ASCII text file using cat, which revealed the password
Bandit Level 13 → Level 14
Level Goal
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level.
Note: localhost is a hostname that refers to the machine you are working on
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
bandit13@bandit:~$ ls
sshkey.private
bandit13@bandit:~$ cat sshkey.private
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAxkkOE83W2cOT7IWhFc9aPaaQmQDdgzuXCv+ppZHa++buSkN+
gg0tcr7Fw8NLGa5+Uzec2rEg0WmeevB13AIoYp0MZyETq46t+jk9puNwZwIt9XgB
ZufGtZEwWbFWw/vVLNwOXBe4UWStGRWzgPpEeSv5Tb1VjLZIBdGphTIK22Amz6Zb
ThMsiMnyJafEwJ/T8PQO3myS91vUHEuoOMAzoUID4kN0MEZ3+XahyK0HJVq68KsV
ObefXG1vvA3GAJ29kxJaqvRfgYnqZryWN7w3CHjNU4c/2Jkp+n8L0SnxaNA+WYA7
jiPyTF0is8uzMlYQ4l1Lzh/8/MpvhCQF8r22dwIDAQABAoIBAQC6dWBjhyEOzjeA
J3j/RWmap9M5zfJ/wb2bfidNpwbB8rsJ4sZIDZQ7XuIh4LfygoAQSS+bBw3RXvzE
pvJt3SmU8hIDuLsCjL1VnBY5pY7Bju8g8aR/3FyjyNAqx/TLfzlLYfOu7i9Jet67
xAh0tONG/u8FB5I3LAI2Vp6OviwvdWeC4nOxCthldpuPKNLA8rmMMVRTKQ+7T2VS
nXmwYckKUcUgzoVSpiNZaS0zUDypdpy2+tRH3MQa5kqN1YKjvF8RC47woOYCktsD
o3FFpGNFec9Taa3Msy+DfQQhHKZFKIL3bJDONtmrVvtYK40/yeU4aZ/HA2DQzwhe
ol1AfiEhAoGBAOnVjosBkm7sblK+n4IEwPxs8sOmhPnTDUy5WGrpSCrXOmsVIBUf
laL3ZGLx3xCIwtCnEucB9DvN2HZkupc/h6hTKUYLqXuyLD8njTrbRhLgbC9QrKrS
M1F2fSTxVqPtZDlDMwjNR04xHA/fKh8bXXyTMqOHNJTHHNhbh3McdURjAoGBANkU
1hqfnw7+aXncJ9bjysr1ZWbqOE5Nd8AFgfwaKuGTTVX2NsUQnCMWdOp+wFak40JH
PKWkJNdBG+ex0H9JNQsTK3X5PBMAS8AfX0GrKeuwKWA6erytVTqjOfLYcdp5+z9s
8DtVCxDuVsM+i4X8UqIGOlvGbtKEVokHPFXP1q/dAoGAcHg5YX7WEehCgCYTzpO+
xysX8ScM2qS6xuZ3MqUWAxUWkh7NGZvhe0sGy9iOdANzwKw7mUUFViaCMR/t54W1
GC83sOs3D7n5Mj8x3NdO8xFit7dT9a245TvaoYQ7KgmqpSg/ScKCw4c3eiLava+J
3btnJeSIU+8ZXq9XjPRpKwUCgYA7z6LiOQKxNeXH3qHXcnHok855maUj5fJNpPbY
iDkyZ8ySF8GlcFsky8Yw6fWCqfG3zDrohJ5l9JmEsBh7SadkwsZhvecQcS9t4vby
9/8X4jS0P8ibfcKS4nBP+dT81kkkg5Z5MohXBORA7VWx+ACohcDEkprsQ+w32xeD
qT1EvQKBgQDKm8ws2ByvSUVs9GjTilCajFqLJ0eVYzRPaY6f++Gv/UVfAPV4c+S0
kAWpXbv5tbkkzbS0eaLPTKgLzavXtQoTtKwrjpolHKIHUz6Wu+n4abfAIRFubOdN
/+aLoRQ0yBDRbdXMsZN/jvY44eM+xRLdRVyMmdPtP8belRi2E2aEzA==
-----END RSA PRIVATE KEY-----
bandit13@bandit:~$ ssh bandit14@localhost -p 2220 -i sshkey.private
Bandit Level 14 → Level 15
Level Goal
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
bandit14@bandit:~$ echo "test" | nc localhost 30000
Wrong! Please enter the correct current password.
bandit14@bandit:~$ mkdir /tmp/tmp.testing/
❯ scp -i key -P 2220 linpeas.sh bandit14@bandit.labs.overthewire.org:/tmp/tmp.testing/
linpeassh 100% 820KB 516.7KB/s 00:01
bandit14@bandit:/tmp/tmp.testing$ cat /etc/bandit_pass/bandit14
MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvS
bandit14@bandit:/tmp/tmp.testing$ echo "$(cat /etc/bandit_pass/bandit14)" | nc localhost 30000
Correct!
8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo
bandit14@bandit:/tmp/tmp.testing$
Explanation
- First tried to send the $RANDOM data to the port 30000 using the nc
- created the temp upload the linpeas.sh and uploaded the script using the scp as we have the private key
linpeas.shfound the password for the bandit14 user stored in the file/etc/bandit_pass/bandit14- submitted it through nc to port 30000. This allowed you to successfully get the password for the next level
Bandit Level 15 → Level 16
Level Goal
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL/TLS encryption.
Note: Getting “DONE”, “RENEGOTIATING” or “KEYUPDATE”? Read the “CONNECTED COMMANDS” section in the manpage.
1
2
3
4
5
bandit15@bandit:/tmp/t15$ echo "$(cat /etc/bandit_pass/bandit15)"| ncat --ssl localhost 30001
Correct!
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
bandit15@bandit:/tmp/t15$
Bandit Level 16 → Level 17
Level Goal
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL/TLS and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
Note: Getting “DONE”, “RENEGOTIATING” or “KEYUPDATE”? Read the “CONNECTED COMMANDS” section in the manpage.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
bandit16@bandit:~$ nmap -p 31000-32000 --script ssl-enum-ciphers localhost
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-28 12:37 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00016s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
31046/tcp open unknown
31518/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 (rsa 4096) - A
| compressors:
| NULL
| cipher preference: client
| warnings:
| Key exchange (secp256r1) of lower strength than certificate key
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| cipher preference: client
|_ least strength: A
31691/tcp open unknown
31790/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 4096) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 (rsa 4096) - A
| compressors:
| NULL
| cipher preference: client
| warnings:
| Key exchange (secp256r1) of lower strength than certificate key
| TLSv1.3:
| ciphers:
| TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| cipher preference: client
|_ least strength: A
31960/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.57 seconds
bandit16@bandit:~$ echo "$(cat /etc/bandit_pass/bandit16)"| ncat --ssl localhost 31518
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
bandit16@bandit:~$ echo "$(cat /etc/bandit_pass/bandit16)"| ncat --ssl localhost 31790
Correct!
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
bandit16@bandit:~$
Explanation
- First lets scan the open ports on the meachine using the nmap with
-popein with ports 31000 to 32000 using the scriptssl-enum-ciphers - As we can see only two ports are lisening with SSL/TLS conneciton
- Echo the password with
ncat --ssl localhost 31790to establish an encrypted (SSL/TLS) connection to a service running on port 31790
The Nmap cheat sheet is available for quick references and commands here.
Bandit Level 17 → Level 18
Level Goal
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
Note: if you have solved this level and see ‘Byebye!’ when trying to log into bandit18, this is related to the next level, bandit19
1
2
3
bandit17@bandit:~$ diff -wy --suppress-common-lines passwords.new passwords.old
x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO | ktfgBvpMzWKR5ENj26IbLGSblgUG9CzB
bandit17@bandit:~$
Bandit Level 18 → Level 19
Level Goal
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
❯ sshpass -p "x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO" ssh -o "StrictHostKeyChecking=no" -p 2220 bandit18@bandit.labs.overthewire.org "bash --norc"
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
ls
readme
cat readme
cGWpMaKXVwDUNgPAVJbWYuGHVn9zl3j8
^C
❯
Explanation
- The command uses
sshpassto provide the password x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO to the ssh command -o StrictHostKeyChecking=nodisables the SSH host key checking, meaning it won’t prompt you about the authenticity of the host (like the warning about adding the host to known_hosts).bash --norcIt will runs the bash shell on the remote machine but skips reading the.bashrcfile using the--norcoption. This avoids any configurations (like auto-logout) that might be present in the .bashrc file.
Bandit Level 19 → Level 20
Level Goal
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
1
2
3
4
5
6
7
8
9
10
11
12
13
bandit19@bandit:~$ ls
bandit20-do
bandit19@bandit:~$ file bandit20-do
bandit20-do: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=368cd8ac4633fabdf3f4fb1c47a250634d6a8347, for GNU/Linux 3.2.0, not stripped
bandit19@bandit:~$ ./bandit20-do
Run a command as another user.
Example: ./bandit20-do id
bandit19@bandit:~$ ./bandit20-do cat /etc/bandit_pass/bandit20
0qXahG8ZjOVMN9Ghs7iOWsCfZyXOUbYO
bandit19@bandit:~$
Explanation
- The files in the directory are listed, revealing an executable file named
bandit20-do. - The
filecommand identifies it as a setuid ELF executable, meaning it runs with the permissions of its owner. - Executing
./bandit20-dowithout any arguments provides information that it allows running commands as another user. - The command
./bandit20-do cat /etc/bandit_pass/bandit20is used to read the password for the next level,bandit20, successfully retrieving the required password.
In the next blog We’ll dive into challenges 11 to 20 and share more practical solutions to help you move forward. Stay tuned!